This article is more than 1 year old
The fastest, most secure browser? Microsoft Edge apparently
Well, in one respect anyway
Microsoft may have taken the decision to ditch the Edge's browser engine for Google's Chromium too soon.
According to the Security Council of Certificate Authorities (CASC), the current Edge browser is in fact the fastest and more secure browser on the market when it comes to identifying and blocking dodgy websites.
The CASC has put out a set of predictions for 2019 – including the claim that more than 90 per cent of the world's http traffic will be secured over SSL/TLS in 12 months' time – but also reviewed where we are in terms in security now.
And, remarkably, it is Edge, rather than Chrome or Firefox that has the, um, edge when it comes to phishing websites.
The industry group gave Edge a "protection score" of 93.6 per cent, compared with just 87.9 per cent for Chrome and 87.0 per cent for Firefox. The score was created by identifying what percentage of phishing sites each browser identified and blocked over time.
Edge succeeded in identifying 98 per cent of phishing sites and the other two just 96 per cent but the key metric was in how fast they did so – because phishers now understand that their sites will be blocked within days and so focus all their efforts into having a big impact as fast as possible.
Edge outperformed Chrome and Firefox when it came to quickly spotting and blocking: It immediately stopped 89 per cent of phishing sites in their tracks; some 10 per cent higher Chrome and 12 per cent more than Firefox.
In two days, Edge had closed off 97 per cent of dodgy sites, with Chrome and Firefox trailing with 95 per cent. Even this improved performance isn't good enough though, complains CASC.
"While browser filters such as Microsoft Smart Screen and Google Safe Browsing do a good job at detecting many phishing sites… most phishing sites are set up and taken down in a matter of hours, not days, this means many thousands of users are not meaningfully protected by browser filters," it said.
Here phishy phishy
Why does this matter? Because, the CASC warns, while some aspects of browser security are getting better, it expects the number of phishing sites to rocket next year. "We predict the problem of encrypted phishing sites that imitate real websites will get significantly worse in 2019," it states.
And it has produced an interesting graph showing the number of malware versus phishing sites from 2012 through to this year. The trends are stark: while malware sites peaked at around 600,000 in 2017, the introduction of new security measures has had a significant impact over 2018, pulling them down to around 100,000. By contrast, phishing has taken off: in one year they have doubled in size from 500,000 to over one million.
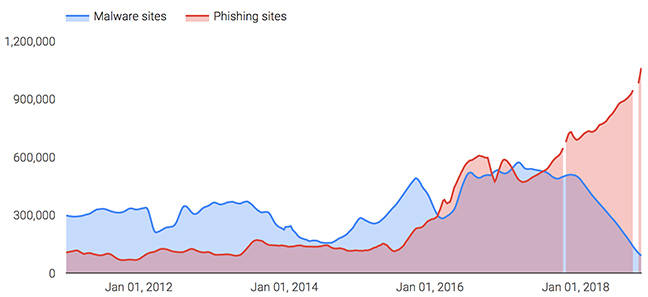
Certificates are killing malware but phishers have found a loophole.
"It's not too dramatic to say there has been an explosion of phishing sites using encryption to trick users," the CASC notes, flagging recent findings from another study that show phishing sites are using anonymous and free TLS certificates to circumvent security checks – at least for a time.
"This growth in encrypted phishing has primarily occurred via Domain Validated certificates," the CASC notes. "These certificates can be acquired via automation [and] are anonymous [with] no identity information required."
It's not hard to see an incentive in the CASC pointed out the phishing problem: If browsers gave its members' certificates a higher level of credibility and/or downgraded free alternatives, they would benefit immediately and companies offering free certificates would face a tougher market.
But the point is still valid: we are getting a more secure internet thanks to secure certificates and browsers put up warnings if websites don't have one, but companies offering free certificates risk undermining that improvement because they have become the focus of online criminals.
Logging
One interesting point in the report: the CASC predicts that in 2019 there will be "a major state-sponsored attack on Certificate Transparency (CT) logs causing Internet outages."
That's referencing Chrome and Safari's requirement that certificates be logged before they are trusted by the browsers. Firefox has said it will join the initiative soon. In order to smooth things, certificate authorities will "pre log" their certificates before they officially issue them so a website is trusted from day one. But the CASC warns, that makes the log a tempting target.
CT logging represents a "single point-of-failure for websites worldwide," the CASC warns, "after all, if a website can’t obtain or renew a certificate recognized as logged and therefore 'trusted' by the browsers, that website will essentially be brought down and can no longer communicate with users."
As such, a denial of service attack on the key CT logs are likely to attract "the kind of attack that a state-sponsor could launch for the purpose of shutting down major websites around the world."
CASC points out that one suspected attack happened just last month, when Google's CT logs were hit hard for over an hour. Google published its post-mortem on the incident this week and noted that the attack was actually the result of additional traffic generated by it migrating the logs from C++ to Trillian: something that its automated system interpreted as an attack.
Regardless, the point remains the same: CT logs could be a very effective way of disrupting the global internet. The CASC didn't offer a solution in its post. ®

